The Cybersecurity Department reminds to stay alert against social engineering email phishing attacks.
- byVic
讀後心得
According to the February report from the Ministry of Digital Development's Cybersecurity Department, a total of 64,531 cybersecurity intelligence reports were collected from government agencies, a decrease of 15,035 from the previous month. It was noted that hackers impersonated the Ministry of Finance to carry out social engineering attacks on government agencies and businesses under the guise of "tax investigations." Additionally, issues related to counterfeit software are severe, necessitating enhanced preventive measures. In February, among the types of threats, information gathering accounted for 39%, while intrusion attacks made up 34%. There were a total of 60 reported incidents, an increase from the previous month, with counterfeit software becoming one of the significant threats. The Cybersecurity Department recommends improving the ability to identify social engineering attacks, particularly by carefully reviewing attachments and links when using external websites to avoid executing malicious programs.
According to the February cybersecurity monthly report published by the Ministry of Digital Development's Cybersecurity Agency, a total of 64,531 cybersecurity intelligence cases from government agencies were collected in February, a decrease of 15,035 cases from the previous month. Notably, hackers impersonated the Ministry of Finance and launched targeted social engineering email attacks on government agencies and enterprises under the pretext of "tax audits." Additionally, the issue of counterfeit software has become increasingly serious, prompting various sectors to raise their vigilance.
The Cybersecurity Agency pointed out that among the cybersecurity intelligence from government agencies in February, the most common type of threat was "information gathering," accounting for 39%. This was mainly achieved through scanning, probing, and social engineering techniques to obtain information. The second type was "intrusion attacks," which made up 34%, mostly involving unauthorized access to systems or privilege escalation. "Intrusion attempts" accounted for 14%, primarily targeting unauthorized hosts for intrusion attempts.
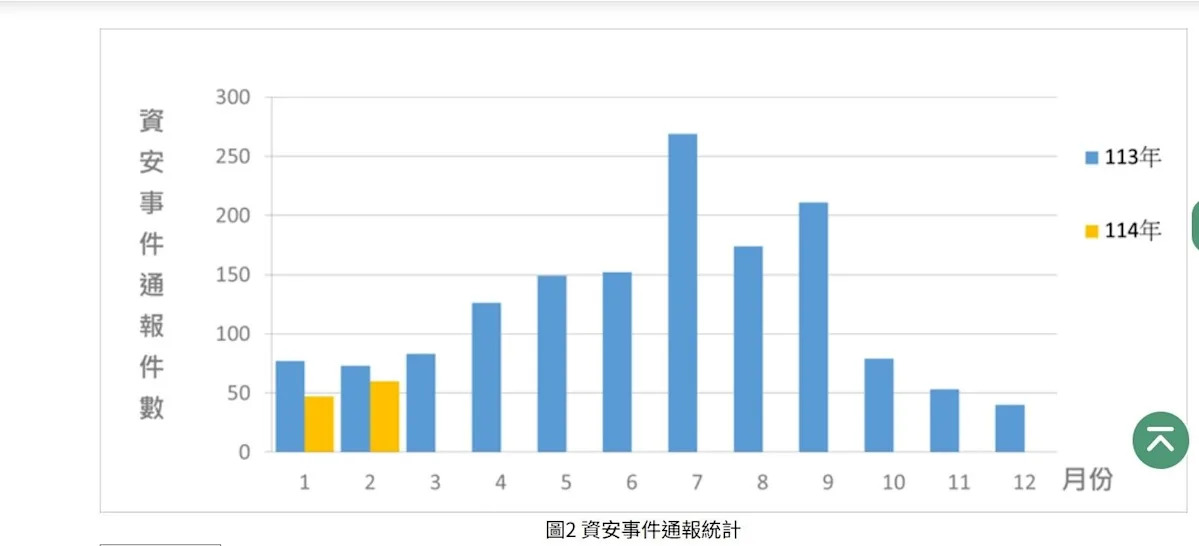
In terms of cybersecurity incident reporting, there were 60 reports received in February, an increase of 13 from the previous month, representing 82.19% of the same period last year. The Cybersecurity Institute discovered several agencies suspected of installing counterfeit software in February, which generated malicious program characteristics, accounting for 20% of the February reports. This indicates that counterfeit software has become one of the significant cybersecurity threats faced by government agencies and requires special attention.
At the same time, monitoring revealed that hackers, impersonating the Ministry of Finance, launched targeted social engineering attacks on government agencies and Taiwanese enterprises. These attacks used "tax audits" as a pretext, specifically targeting financial personnel with access to sensitive information, enticing them to open and click attachments containing malicious links. Relevant intelligence has been provided to various agencies as a reference for collaborative defense and monitoring protection.
The Cybersecurity Agency noted that in response to social engineering attacks, recent hackers not only launched attacks via email or government website functions but may also utilize external websites used by agencies, such as job search sites, cloud file-sharing services, and social media platforms, to send malicious files or links. By exploiting the credibility of these websites, they entice users to download and execute malicious programs, thereby infiltrating internal networks.
To reduce the risk of related attacks, the Cybersecurity Agency recommends that government agencies enhance their ability to identify social engineering attacks, particularly when using external websites. They should carefully review attachments and links to avoid executing malicious programs due to misjudgments based on file names, icons, or document formats.

In terms of cybersecurity incident reporting, it was found that several agencies suspected of installing counterfeit software in February accounted for 20% of the reports for that month. This shows that counterfeit software has become one of the important cybersecurity threats faced by government agencies.